navigation

Originally published July 15, 2021, updated June 26, 2023
Imagine you’re hard at work, but the computer is running terribly slow, your files won’t open, and you’re bombarded with error messages. Then to add to your frustration, you get called into an emergency meeting. There, IT announces the company was hit with ransomware. Ouch.
Cybercriminals have multiple ways to exploit system vulnerabilities to gain access to proprietary company data, personally identifiable information, and other sensitive data. Attack vectors can include everything from viruses, malware, malicious software or attachments, websites, and acts of social engineering. However, one cyber threat stands out from others as the most sophisticated and disastrous, and that is ransomware.
That scenario plays out every day in companies all over the globe. Ransomware attacks, where cybercriminals hold data hostage for ransom, are a constant threat to B2B businesses, especially with the increasing popularity of B2B eCommerce.
In the last year, ransomware attacks increased in number and degree of sophistication. According to Verizon’s DBIR 2021 data breach investigations report, 1 in 10 of all cyberattacks now involve ransomware. Furthermore, the global cost of ransomware is increasing year over year and, according to Cybersecurity Ventures, is estimated to reach a staggering $265 billion by 2031.
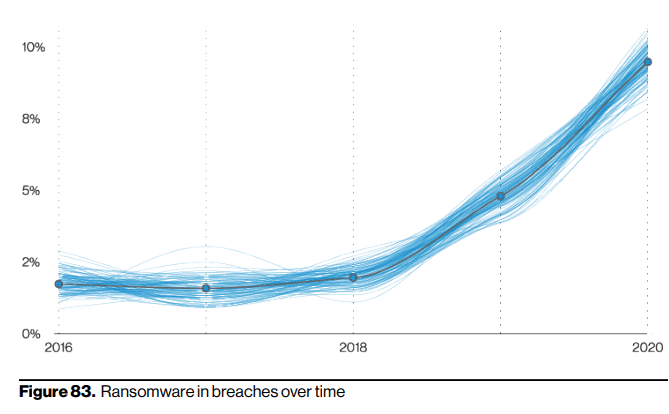
[Source]
Fortunately, with the right tools and strategy, you can shield yourself from these threats. In this post, we’ll give you a comprehensive overview of eCommerce site security. We’ll explain what is security in eCommerce all about, go over some of the latest eCommerce and security trends, and talk about real-world cybersecurity problems faced by B2B brands today. Later in the article, we’ll list various types of eCommerce security issues, how to stay protected, and maintain a culture of digital literacy. You’ll leave with everything you need to know about the security in eCommerce.
What is eCommerce security?
eCommerce security refers to the measures and protocols put in place to protect online transactions and sensitive customer information, like credit card details or login credentials, during eCommerce activities. It involves safeguarding the integrity, confidentiality, and availability of data, as well as preventing unauthorized access, fraud, and cyber threats.
ECommerce security measures include implementing secure payment gateways, encryption technologies, firewalls, and robust authentication processes to ensure that customer data and financial transactions are securely handled throughout the entire eCommerce process. By prioritizing eCommerce security, businesses can establish trust with their customers and safeguard their sensitive information from potential threats.
What Is Ransomware?
Criminals use ransomware to encrypt and incapacitate their victim’s data and then hold the data hostage until they receive compensation. Even then, making payment may or may not guarantee that access will be restored.
There are many types of ransomware. Scareware typically involves a phony message that reports a malware discovery and demands a sum to remove it.
Screen lockers are malware that denies users access to their computers.
By far the most dangerous type of ransomware for B2B businesses, however, is encryption ransomware. With this method of attack, criminals encrypt your files and demand payment in exchange for decryption.
Once criminals gain control of critical files, system restore or security scanners are powerless. To shield themselves from these eCommerce security threats, B2B businesses must recognize that their online business may be a target, identify possible lines of attack, and then implement preventive measures.
Why Is Ransomware a Problem in B2B eCommerce?
The pandemic accelerated the move of more activities online. Now we consume entertainment, work, and shop digitally. Never-before-seen B2B eCommerce trends are pushing brands to explore new go-to-market strategies and selling channels. Many B2B businesses entered the eCommerce arena for the first time and were forced to adopt new selling methods and new ways of meeting customer expectations on the fly.
During this time, manufacturers, distributors, and wholesalers were focused on alleviating the ongoing strains on their supply networks. With attention diverted to keeping the doors open and the supply chain intact, security fell a few rungs on many company’s priority ladders. Malicious actors are now taking advantage of these lapses to gain access to the data and processes central to business operations.
That can include any attempt to modify a system in a way that affects its operation and benefits the attacker. From exploiting unpatched vulnerabilities to social engineering, DDOS attacks, malware, and viruses, there are many ways to compromise business systems.
Ransomware deprives B2B businesses of the data and systems they need to perform critical functions. As fraud, attacks, and other crime becomes more sophisticated and destructive, the monetary value of ransomware increases. Not surprisingly, there is an ongoing debate on whether to pay the ransom or attempt an independent recovery. Aside from the financial impact, there’s also damage to reputation, and loss of customer trust.
Ransomware facts, trends, and statistics
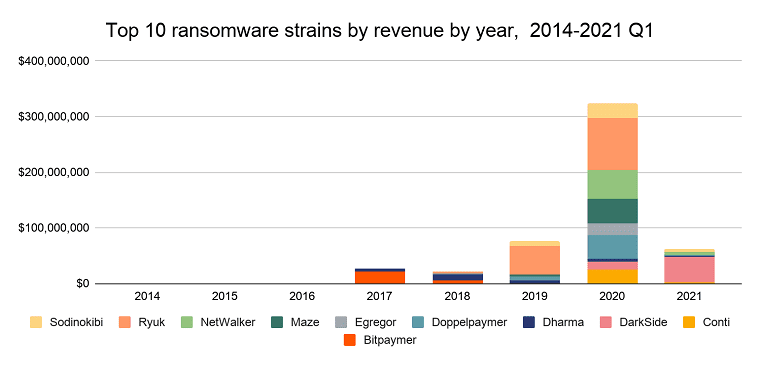
- Ransomware attacks are exploding. In 2020 alone, ransomware netted attackers over $300 million, and we expect to see similar numbers in 2021.
- Ransomware is increasingly profitable. Prior to 2020, there were no ransomware payments above $6 million; now, that sum is paid at least once a quarter.
- Cryptocurrency is a popular method of payment for ransomware attacks. Blockchain data shows that the total amount paid by ransomware victims increased by 336% in 2020 to nearly $370 million.
- Criminals gain additional leverage by threatening to leak data on the dark web if victims refuse to pay. Such attacks are gaining prevalence, with manufacturing being the most targeted industry.
- Ransomware attacks erode consumer confidence, leading to a rapid decline in business. According to Arcserve, 59% of consumers would take their business to a competitor if they learned the business had suffered a cyberattack.
- To make a bad situation worse, if the attackers access data that constitutes a breach under regulations such as GDPR, HIPAA, or CCPA, the victim may also be subject to fines from regulators.
- Governments and law enforcement warn that making ransomware payments can result in trouble with the law. What’s more, insurance providers are suspending ransom payouts, which places victims in an even more precarious position.
What B2B eCommerce Businesses Are At Risk?
Originally, cyberattacks were aimed at single computer systems or individual users. When online selling was in its infancy, unpatched eCommerce shopping site security risks were the low-hanging fruit for criminals looking to steal money. Over time, cybercriminals realized there was more money in targeting businesses.
Today, attackers are more sophisticated and organized than ever. They target the industries and groups they believe will net them more disruption, greater negotiating power, and higher chances of large ransom payments.
Here are some business types at a heightened risk of attack.
Businesses in western countries. Cybercriminals go where the money is, which means favoring B2B eCommerce businesses and supply chains in countries like the UK, US, and Canada. They could target businesses with poorly protected payment systems and those lacking eCommerce PCI compliance. Attackers understand organizations with low levels of digitalization and their less digital-savvy clients are more likely to pay up.
Large companies. Cyberattacks on large, established businesses are some of the most common. Usually, a hacker will begin by identifying crucial elements, then perform surveillance that allows them to study employee patterns and processes, and pinpoint the weakest security link. This approach lets the perpetrators select the ideal industry, company, monetization concept, and attack vector for a successful breach.
Small to medium businesses. Many businesses are moving online for the first time, and just beginning to explore digital commerce. Many also falsely assume they’re too small to be targeted. However, a small ransom of a few hundred dollars obtained from numerous businesses represents a tidy sum to criminals. One such attack on IT firm Kaseya demanded $70 million in cryptocurrency to unlock all affected businesses at once.
Disrupted organizations faced. COVID-19 restrictions forced many business and governmental agencies to move online quickly. Those lacking a complete digital strategy are less prepared to deal with the implications of adverse outcomes. Criminals understand these dynamics and favor universities, school boards, and government institutions as targets. According to data by Sophos, retail and education industries experience the highest number of attacks.
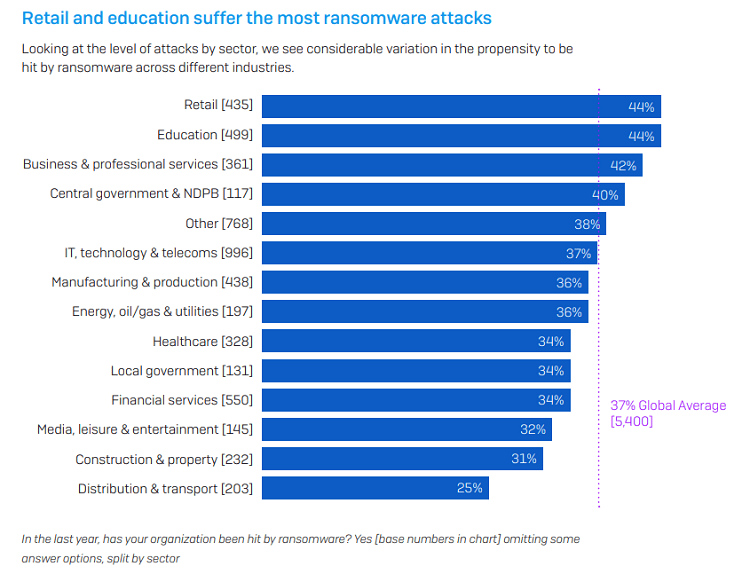
Entities serving critical functions. Infrastructure and healthcare organizations are prime targets since service interruptions could literally mean the difference between life and death. In fact, 2020 saw the highest number of attacks against the healthcare sector. Hundreds of healthcare providers were impacted, which led to billions of dollars in recovery costs.
Businesses holding critical information. Law offices and police departments hold valuable, confidential, and personal information. Banking institutions and financial services literally hold financial assets, so they’re also at risk of data theft and extortion-style attacks.
It’s also important to note that extortion is on the rise even when data is not encrypted. Attackers simply threaten to publish data if the ransom is not paid. Since encryption and decryption are not necessary, this requires less effort for the same result.
eCommerce Security Threats
As mentioned earlier, there are virtually limitless ways to expose, modify, disable, or devastate any given system. For online sellers especially, everything, not just physical computer systems, but also software, networks, and infrastructure, are at risk of eCommerce security breaches.
According to cyber threat intelligence Sean Nikkel, senior cyber threat intelligence analyst at Digital Shadows, the institutional and industrial sectors present an appealing target for multiple reasons. “There’s an incredible return on investment from enterprises in the industrial sectors, specifically those involved with energy and petroleum.”
These enterprises require availability and would rather pay the ransom than lose access and cause a domino effect of damages. A single outage, like the recent Colonial Pipeline attack, can create supply chain interruptions and shortages, disruption of essential services, rising prices in grocery stores, and impacts on the everyday consumer.
If you’re selling to businesses online, you can’t afford to overlook any security aspects in eCommerce, no matter how minor. Unlike B2C eCommerce sellers, B2B sellers deal with more complex products, a more diverse customer base, and manage larger order volumes. High order values and customer loyalty also catch the attention of cybercriminals. Because they can cause more damage, they can demand more compensation in return.
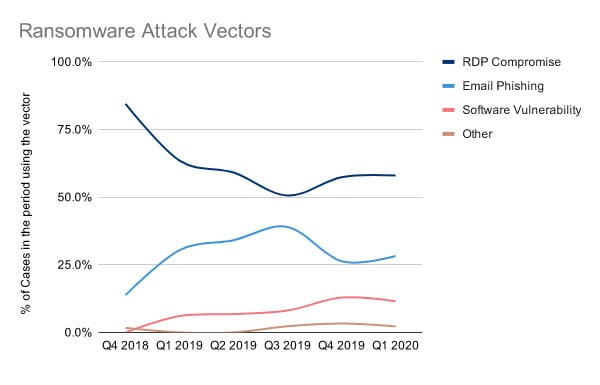
Here are the most widespread ransomware attack vectors and some recent examples.
[Source]
Stolen credentials and brute force
A brute force attack is a relentless attack by trial and error. These attacks are usually automated, and standard methods involve guessing potential usernames against a password or passwords, or utilizing valid credentials (stolen from other breaches) and trying them across multiple systems.
The shutdown initially caused large supply chain disruptions across the New South Wales region. According to farmer Gabrielle Coupland, it’s not just the farmers whose livestock kill dates were disrupted, it’s the truck drivers, stock handlers, and the necessary re-organizing that had to be done.
Security expert SecurityScorecard first observed an unsuccessful intrusion attempt through a remote desktop protocol request and identified half a dozen JBS employee authentication credentials available on the dark web as early as the beginning of 2021. According to the security expert, this points to reconnaissance activity where attackers assessed possible system entry points.
Remote desktop compromise
The pandemic led many organizations to switch to remote operations. Working from home increases the risk of exposed remote desktop protocol (RDP) ports. These ports are generally used by enterprises and support teams to access company resources or troubleshoot employee systems. There’s a nasty side effect, however. RDPs are a common way for attackers to control a computer system remotely.
In this attack, cybercriminals gained access to the plant’s troubleshooting system. According to federal and Pinellas County authorities, the operator noticed an attacker remotely accessing the workstation, opening various programs on the screen. While the attack was thwarted before the water supply could be compromised, it demonstrates the seriousness of cyberattacks on critical infrastructure.
Phishing and spear phishing
Phishing and spear phishing are social engineering attacks that target individuals in organizations to harvest credentials. Criminals commonly target non-executive members with business email compromise (BEC) attacks. That’s where attackers impersonate email account owners to gain access to servers where critical information is located.
According to Cybersecurity and Infrastructure Agency (CISA), the likely culprit was a phishing email by DarkSide ransomware group that tricked an employee into downloading malware. Judging from DarkSide’s previous attacks, it’s likely that the attack vector was a malicious email link or malicious document macro. The ensuing disruption triggered price hikes and panic buying in the Southeastern US which resulted in shortages. Ultimately, Colonial paid the attackers $4.4 million to resume operations.
Software vulnerabilities
Cybercriminals are constantly on the lookout for security gaps, from poorly defended infrastructure to software weaknesses. They attempt SQL injections to gain access to web applications. They also seek out vulnerabilities in third-party tools. When systems are unprotected or software isn’t updated with the latest patches, businesses are exposed without knowing it.
According to Walter Tong, a security architect at the Georgia Technology Authority, Atlanta was the ideal target. An audit performed two months prior identified thousands of severe security vulnerabilities and nearly 100 government servers running Windows Server 2003 that Microsoft stopped supporting in 2015.
Initially, the city of Atlanta devoted $2.7 million to recover from the attack, and the sum later ballooned to $9.5 million. Sophisticated attacks increase the costs to victims. Downtime, lost opportunity, human costs, device costs, network costs, and ransoms paid all contribute to the high costs of remediation.
Sustaining the attack: network propagation
Any malware that enters a network must scan for shared files and accessible points to infect other computers within the system. Internal processes such as file sharing and data synching can also propagate the attack.
In either case, malware replicates and spreads until it is stopped by security or runs out of areas to infect. If data and systems aren’t separate, attackers can bring entire IT departments down.
According to DoublePulsar, Kaseya was designed to allow the administration of systems with high-level privileges. Attackers pushed a management agent update that automatically installed itself on managed systems without any resistance. While this attack affected only 0.1% of Kaseya’s customers, it highlights the importance of segregating data, systems, and access.
Businesses moving online for the first time or making the move to remote work can unwittingly set lax work from home policies or provide inadequate security training. Files downloaded at home may be shared with the home office and other connected machines. And, if files are set to automatically sync when added and changed, a malicious virus can quickly spread and infect all computers in the network in seconds.
B2B eCommerce Security Best Practices
Today, data is the lifeblood of any B2B eCommerce business. Like digital kidnappers, attackers are drawn to nabbing data and holding it hostage in exchange for money. Besides monetary gain, humiliation, competitive espionage, and even political ideologies are powerful motivators. So how do you go about securing your eCommerce website? Below, we’ll go over the different eCommerce security tools, some best practices to prevent an attack, and what to do if one happens.
Backup and recovery
With the sheer volume of data used by businesses today, concerns arise about getting exposed to attacks. However, unlike paying a ransom, restoring data from backups is guaranteed, will not cost you more money, and will not potentially get you in trouble with the law.
There are many data backup tools available, from open source to proprietary. But successful backups are supported by the proper processes. Set your backup frequency to fulfill your recovery point objective. Store backups in protected storage on an isolated network. Otherwise, there’s no guarantee that even the best backup solutions will deliver the desired results. Lastly, backups should be tested regularly to identify issues, measure recovery times, or determine if data can be recovered at all.
Network segmentation
Attackers primarily target open or local networks and machines, so it’s essential to keep critical files isolated from local and open networks. This can include steps such as physically removing disks or maintaining separate servers.
Offline backups must not be accessible by other systems to prevent access by an attacker. Your architecture and operational processes must support network segmentation using existing tools. Otherwise, one compromised component will act as a conduit and infect other systems. Review your IP tables, firewall, router rules, as well as VLAN settings to prevent this method of attack.
Software updates
Sometimes, all it takes is a lapse in the update process. Attackers often take advantage of little-known vulnerabilities, many of which have working patches available.
An increasingly large number of connected systems and applications makes it a challenge for B2B sellers to keep track of updates. But it’s critical to eliminate known vulnerabilities quickly. Many tools help you do this, but the process is just as important. Ensure your monitoring, patching, and update activities stay current and create processes for testing, delivery, and deployment of patches as they are released.
Layered security
In the face of heightened extortion-based attacks, it’s more important than ever to stop unauthorized data access. Don’t settle for a mere textbook definition of encryption. Enable additional layers of protection to block attackers at different points of entry.
Also, don’t rely solely on your security software. While security technology excels at deduction or automating threat discovery, there are still certain things only a human eye can catch. If you don’t have the human resources on hand, consider hiring cybersecurity specialists to uncover flaws in your systems.
Employee education
No matter what steps you take, you must always stay informed. The human element remains the single greatest vulnerability, and criminals remain eager to exploit it. Social engineering remains a popular attack vector, so it’s important to stay on top of the latest developments and train team members on detecting suspicious activities, websites, emails, texts, and more.
At Oro, we train all our employees on cybersecurity, not just our IT department. Every employee at every level is taught to be vigilant and to recognize suspicious activities. Having a recovery plan and ensuring everyone understands it also goes a long way in mitigating the costs, disruption, and damage if an attack does occur.
Don’t pay the ransom
Finally, if you do get hit by ransomware don’t rush to make the payment. It’s natural for regaining access to your data to be the first thing that comes to mind. However, payouts empower attackers, validate their business model, and incentivize others to join the trade. Paying ransoms doesn’t guarantee the quality of returned data nor its completeness. It also marks you as someone who is willing to pay and sets you up for future attacks.
Aside from ethical considerations, paying the ransom may not be the most effective way to restore access to your data. If you do decide to pay, perform a cost/benefit and a statistical analysis to determine how much data the attacker can give back to you.
Two experts discuss how to get security right for B2B eCommerce
OroCommerce Security Technologies in eCommerce
B2B eCommerce platforms are designed for complex B2B sales and ordering processes. The right platform will support flexibility and customization, meaning greater control of your performance, data, and security.
In other words, it will already come with several security measures for your eCommerce website. OroCommerce and OroMarketplace are both B2B eCommerce platform solutions built with security in mind. These solutions empower you to craft a security strategy that meets your industry requirements and needs. With features like robust access controls, admin-server segregation, and deploy anywhere policy, you get the peace of mind that critical business data is in safe hands.
Let’s dive into some of the security measures used in eCommerce.
SOC 2 compliance
Service Organization Controls (SOC 2) is a reporting mechanism designed for service providers that store customer data in the cloud. In February of 2020, Oro fulfilled the Security and Availability component including network security, intrusion detection, and other system security analyses. This year, Oro’s SOC 2 Type 2 audit was updated, which is a further evaluation and validation of internal controls policies over a 6 to 12 month period.
PCI DSS compliance
If you accept any payment card or credit card, you need an SSL certificate and comply with the Payment Card Industry Data Security Standard (PCI DSS) requirements. Oro keeps up to date and is compliant with the latest changes in PCI for all its cloud-based eCommerce software products and services.
Secure hosting
Cloud systems allow B2B eCommerce businesses to securely archive, backup and manage their systems in the cloud. Oro’s cloud service provides firewall protection, security solutions, and is manned 24/7 by live support teams. Integrate with any payment gateway in eCommerce and ensure the security of your transactions.
Hourly backups
Many businesses must cease operations once they lose access to their product, customer, or financial information. Oro offers hourly cloud backups to ensure your business always has up-to-date data in case something goes wrong.
Brute force protection
A large percentage of data breaches are a result of brute force attacks or credential theft. OroCommerce and OroMarketplace are designed to make backups inaccessible from the production environment, minimizing this attack vector.
Encryption protection
Just like encrypting your wi-fi connection, your Oro eCommerce applications can run on encrypted desktops and laptops to further protect stored data. In the event of breaches or even physical theft of devices, your critical data won’t be affected.
Segregation of duties
The Oro application admin panel features extensive segregation of duties. With powerful access restriction features, businesses can delegate access requirements to authorized individuals only.
The power of open source
The open-source nature of Oro products means that updates are screened by a large ecosystem of developers. In this respect, Oro eCommerce products are more secure than comparable proprietary software, as the process of identifying security risks, testing, and fixing issues is more controlled, more thorough, and more widely reviewed and validated.
So Why Is Security Important in eCommerce?
No one expects a cyberattack. If you are unfortunate enough to become a victim, recovering won’t be cheap. You’ll not only lose access to data required to operate, but you’ll also need to eventually reinstate that data and then face costly and time-consuming remediation.
It’s worth noting that businesses increasingly depend on a patchwork of integrations, third-party and fourth-party vendors. All that poses a huge cybersecurity risk to you and your customers.
In one of 2020’s highest-profile cases, Maersk, a Danish shipping giant, reinstalled 4,000 servers and 45,000 PCs, suffering losses of up to $300 million.
The good news is that you’re not alone. As more organizations start their digital transformation journey, invest in new digital technology, or continue operating remotely, eCommerce safety and security will remain a priority. The web is also full of literature and resources on security schemes in eCommerce. Ensure you have the necessary processes and eCommerce security solution
to manage backups, cyber risks, phishing, and ransomware.
When it comes to security, Oro is the optimal choice – it allows you to focus on growing your B2B eCommerce business safely and worry-free.
Read an industry-leading analyst report to make a more informed B2B eCommerce investment decision
Questions and Answers
What is the impact of ransomware on B2B eCommerce?
Ransomware incidents impact B2B eCommerce business processes leaving them without the data they need to operate, deliver products and services, and collect payment.
What are the main B2B eCommerce security considerations?
Ransomware incidents impact B2B eCommerce business processes leaving them without the data they need to operate, deliver products and services, and collect payment. Simple eCommerce transaction security measures are not enough, and online brands must protect multiple areas of their business from data breaches.
How can B2B eCommerce businesses stay protected from ransomware?
Online sellers can start with backing up their data and updating software regularly. They should control transactions, practice segmentation of duties, and monitor their networks for suspicious activity. Lastly, they can educate employees on downloading items from known sources and double-checking emails.
How do security measures impact the customer experience in eCommerce?
Security measures play a crucial role in enhancing the customer experience in eCommerce. By implementing robust security measures, such as secure payment gateways, encryption technologies, and strong authentication processes, customers can feel confident and trust that their personal and financial information is protected. When customers have a positive experience with secure transactions, they are more likely to continue engaging in eCommerce activities.